



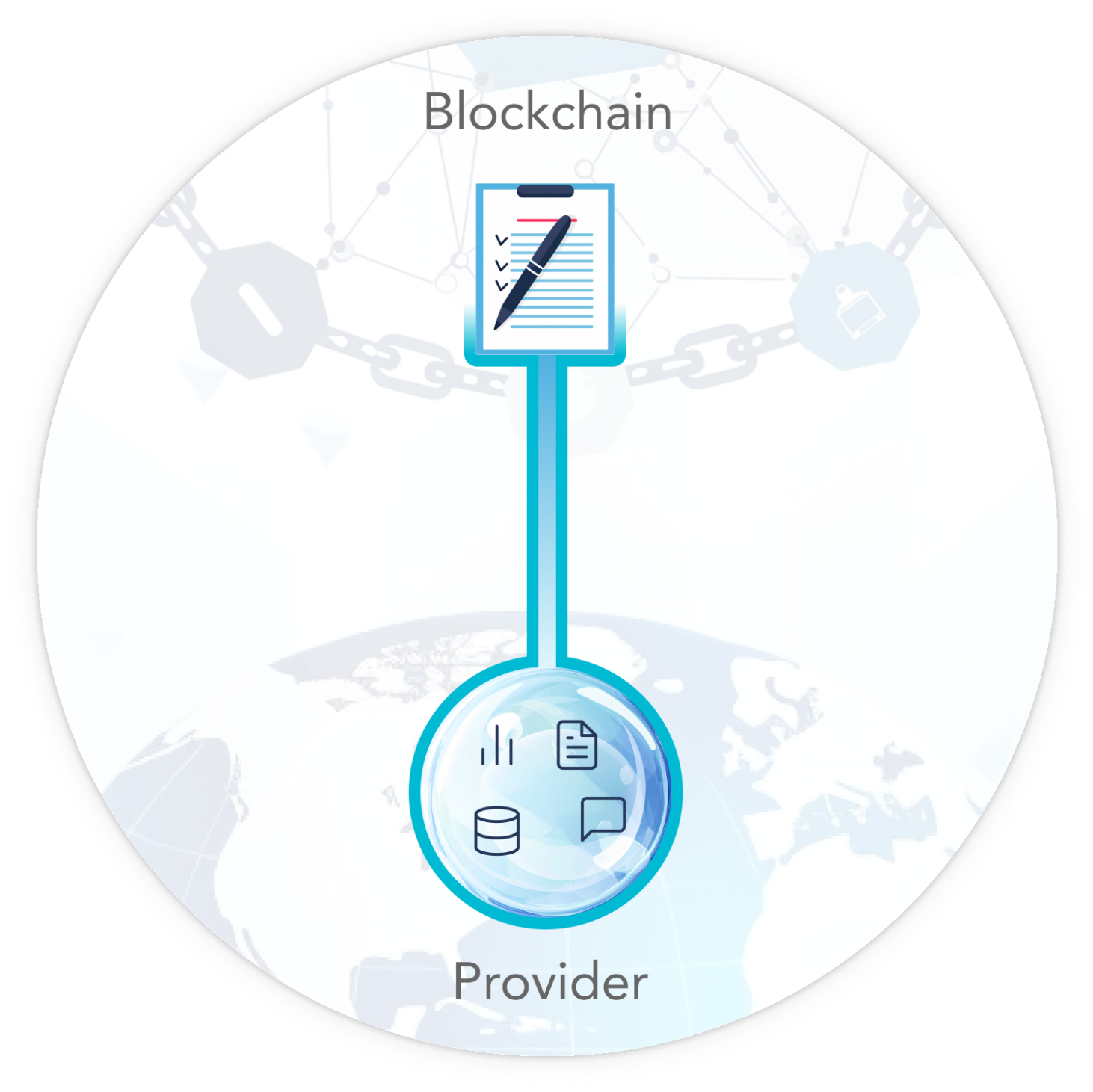
Bubble Protocol stores content in off-chain bubbles. A bubble is a secure vault containing files and directories whose access permissions are managed by a smart contract. The bubble itself is hosted by a provider chosen by the user (see Bubble Providers). Whenever content is requested from the bubble, the protocol checks the access permissions from the smart contract, only permitting the request if the requester has the appropriate permissions.
The smart contract for a bubble is designed specifically for each use case and can be as simple or as complex as needed to control the content throughout its life. Once the smart contract indicates the bubble has been terminated, the off-chain bubble is ‘popped’ and all its content is deleted.
Each bubble is uniquely identified by its smart contract address, blockchain id and host provider. Each piece of content hosted by the protocol is uniquely identified by its bubble id and 32-byte file id (often the file id is defined as the content hash). The smart contract specifies separate read/write/append/execute permissions for each user address and 32-byte file id. This way each file can have different access permissions for every user.
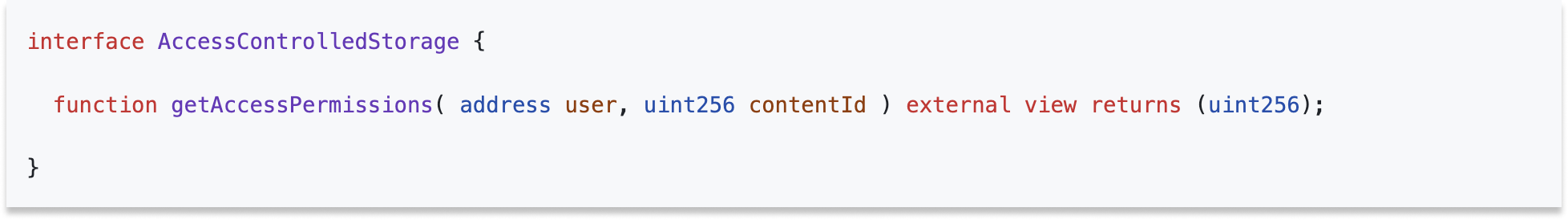
Any smart contract can be used to control a bubble provided it implements the following interface:
Bubbles are stored on a provider of the user’s choosing.
By design, Bubble Protocol specifies the protocol for how bubble content is protected, not how the bubble is stored. This means the protocol can be used with private servers, public cloud servers or decentralised peer-to-peer storage networks, and can support one or multiple blockchains:
- The Bubble Private Cloud is a public cloud provider run by Bubble Protocol that supports multiple blockchains.
- The Bubble Cloud Cooperative is a social movement to bring independent cloud storage providers together into a cooperating network to improve redundancy and decentralisation.
- The Bubble Network will be a decentralised peer-to-peer network with Bubble Protocol built in.
- Home providers can provide private bubble storage exclusively for family and friends.
- Company providers can use existing business infrastructure exclusively for registered customers, employees and suppliers. This approach allows data to be kept in-house, enabling Web3 capabilities without compromising on security or reinventing company infrastructure.
Anyone can become a bubble provider by deploying a server running Bubble Protocol’s open-source Guardian library or by integrating the Guardian into existing infrastructure. The Guardian acts as a gateway to the underlying bubble storage layer, authorising requests based on the permissions defined in the bubble’s smart contract. The Guardian does not specify the underlying storage mechanism, allowing the protocol to be used with file systems, databases, content delivery networks, object storage systems, archival storage services and other infrastructure.
Content within a bubble can be public or encrypted. Content encryption is managed by a client encryption policy, which specifies the encryption method, if any, for each piece of content within the bubble. Encryption policies are fully customizable, allowing the developer to choose one or more encryption methods and to specify which content is encrypted. Bubble Protocol ships with AES-GCM encryption out of the box.
A bubble's smart contract defines which users are permitted to access which content within the bubble. For encrypted bubbles, Bubble Protocol provides support for multiple users, allowing each user to decrypt the bubble contents with their private key. This removes the inconvenience and security concerns of pre-sharing encryption keys with all users of a bubble.
The Bubble Network is a decentralised peer-to-peer bubble provider currently under construction. It will be a fully decentralised off-chain storage network, like IPFS, but with access controls and token-based storage payments. It will form an ideal off-chain storage layer for Web3 applications, supporting both public and private data storage, permissioned data access, content deletion and data sharing capabilities, all in a fully decentralised manner. The network will not replace other bubble providers but will run alongside them, giving users, developers and businesses a full suite of options for Web3 storage.